VIRUS ALERT!
Destructive malware “CryptoLocker” on the loose –
ransomware known as Cryptolocker, and other aliases.
This ransomware is particularly nasty because infected users and networks are in danger of losing their personal and business files forever.
CryptoLocker is a ransomware trojan which targets computers running Microsoft Windows[1] and first surfaced in September 2013. A CryptoLocker attack may come from various sources; one such is disguised as a legitimate email attachment. When activated, the malware encrypts certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware’s control servers. The malware then displays a message which offers to decrypt the data if a payment (through either Bitcoin or a pre-paid voucher) is made by a stated deadline, and threatens to delete the private key if the deadline passes. If the deadline is not met, the malware offers to decrypt data via an online service provided by the malware’s operators, for a significantly higher price in Bitcoin.
Although CryptoLocker itself is readily removed, files remain encrypted in a way which researchers have considered infeasible to break. Many say that the ransom should not be paid, but do not offer any way to recover files; others say that paying the ransom is the only way to recover files that had not been backed up. Payment often, but not always, has been followed by files being decrypted.
CryptoLocker typically propagates as an attachment to a seemingly innocuous e-mail message, which appears to have been sent by legitimate company; or, it is uploaded to a computer already recruited to a botnet by a previous trojan infection.[2] A ZIP fileattached to an email message contains an executable file with the filename and the icon disguised as a PDF file, taking advantage of Windows’ default behaviour of hiding theextension from file names to disguise the real .EXE extension. Some instances may actually contain the Zeus trojan instead, which in turn installs CryptoLocker.[3][4] When first run, the payload installs itself in the Documents and Settings folder with a random name, and adds a key to the registry that causes it to run on startup. It then attempts to contact one of several designated command and control servers; once connected, the server then generates a 2048-bit RSA key pair, and sends the public key back to the infected computer.[1][3] The server may be a local proxy and go through others, frequently relocated in different countries to make tracing difficult.[5][6]
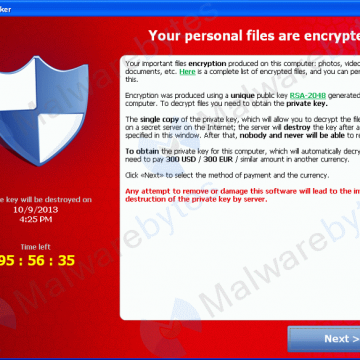
The payload then proceeds to begin encrypting files across local hard drives andmapped network drives with the public key, and logs each file encrypted to a registry key. The process only encrypts data files with certain extensions, including Microsoft Office, OpenDocument, and other documents, pictures, and AutoCAD files.[4] The payload then displays a message informing the user that files have been encrypted, and demands a payment of 300 USD or Euro through an anonymous pre-paid cash voucher (i.e. MoneyPak or Ukash), or an equivalent amount in Bitcoin within 72 or 100 hours (while starting at 2 BTC, the ransom price has been adjusted all the way down to 0.3 by the operators to reflect the fluctuating value of Bitcoin),[7] or else the private key on the server would be destroyed, and “nobody and never [sic] will be able to restore files.”[1][3]Payment of the ransom allows the user to download the decryption program, which is pre-loaded with the user’s private key.[3] Some infected victims claim that they paid the attackers but their files were not decrypted.[2]
In November 2013, the operators of CryptoLocker launched an online service which claims to allow users to decrypt their files without the CryptoLocker program, and to purchase the decryption key after the deadline expires; the process involves uploading an encrypted file to the site as a sample, and waiting for the service to find a match, which the site claims would occur within 24 hours. Once a match is found, the user can pay for the key online; if the 72-hour deadline has passed, the cost increases to 10 Bitcoin.[8][9]
A new variant of CryptoLocker identifying itself as “CryptoLocker 2.0” was discovered in December 2013; it contains a few notable differences, such as a payload disguised as akeygen program uploaded to a P2P site, its use of an RSA-1024 key with a Triple DESalgorithm, only accepting Bitcoin, additional encrypted file types (such as media files), and the ability to spread via removable drives. However, analysts believed that due to some architectural and behavioral differences between the two versions (such as being written in C# instead of Visual C++, and its slightly different behavior), the author of CryptoLocker 2.0 may not be connected to the original author of CryptoLocker.